 (Hackers compromised the Federal Bureau of Investigation’s external email system on Saturday. (Jose Luis Magana/AP)
(Hackers compromised the Federal Bureau of Investigation’s external email system on Saturday. (Jose Luis Magana/AP)
Hackers compromised the Federal Bureau of Investigation’s external email system on Saturday, sending spam emails to potentially thousands of people and companies with a faked warning of a cyberattack.
The FBI said in a statement it was “aware of the incident this morning involving fake emails from an @ic.fbi.gov email account” but declined to provide further details. “The impacted hardware was taken offline quickly upon discovery of the issue,” the FBI said. It did not respond to an emailed request for more information.
Cybersecurity experts said the fact that the email didn’t include any malicious attachments could indicate the hackers stumbled across a vulnerability in the FBI portal and didn’t have a particular plan to exploit it.
“It could have just been a group or individuals looking to get some street cred to tout on underground forums,” said Austin Berglas, a former assistant special agent in charge of the FBI’s New York office cyber branch, who is not involved in any government investigation of the incident. “I would think that it would be some sort of criminal group or some sort of ‘hacktivist’ group,” rather than a coordinated state-backed attack.
The compromised system was an unclassified server used by FBI personnel to communicate outside of the organization, and the hackers didn’t appear to have gained access to internal databases containing state secrets or classified information, said Berglas, who is now global head of professional services at cybersecurity firm BlueVoyant.
A copy of the alleged spam email was posted on Twitter by the Spamhaus Project, an international watchdog that tracks spam and related cyberthreats such as phishing, malware and botnets. The subject line was: “Urgent: Threat actor in systems,” and the email claimed to be a warning from the Department of Homeland Security about a cyberattack.
Spamhaus, which analyzed the emails’ metadata, wrote on Twitter that the fake emails were “causing a lot of disruption because the headers are real, they really are coming from FBI infrastructure.” They were apparently sent to thousands of addresses, at least some taken from the American Registry for Internet Numbers database, the nonprofit responsible for managing the distribution of Internet addresses in the North American region.
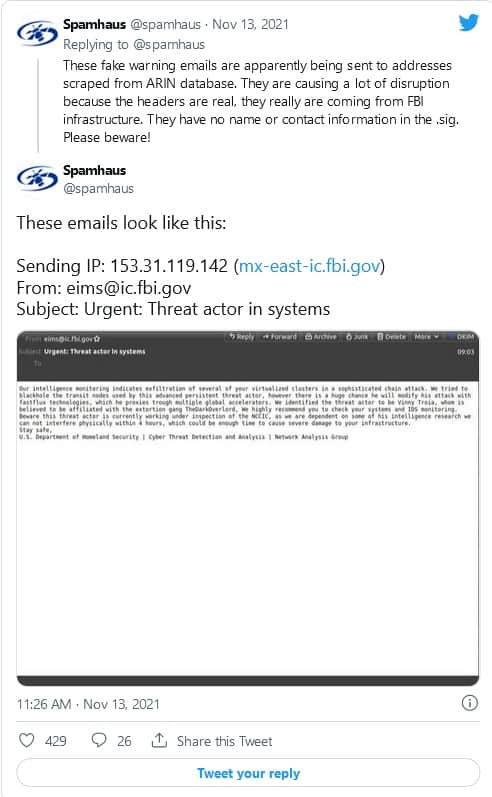
The email made reference to an international hacker group called the Dark Overlord, which allegedly steals data and demands big ransoms for its return. The group purportedly stole students’ records in several U.S. states and episodes of Netflix shows in 2017. A British man was sentenced to five years prison for his role in the hacking group last year.
The email claimed that the “threat actor” appeared to be cybersecurity expert Vinny Troia. Troia published an investigation of the Dark Overlord last year.
Troia couldn’t immediately be reached for comment. On Twitter, he speculated that he may have been the subject of what he called a smear attack. “Should I be flattered that the kids who hacked the @FBI email servers decided to do it in my name?” he wrote.
Although online scammers often create fake emails purporting to be from official sources, it is highly unusual for a hacker to penetrate a government server — and experts say the incident highlights the vulnerabilities of email communications.
Russian government hackers last year breached the Treasury and Commerce departments, along with other U.S. government agencies, as part of a global espionage campaign, and Chinese government hackers are believed to have compromised dozens of U.S. government agencies.
“It could have been a lot worse,” said Berglas. “When you have ownership of a trusted dot-gov account like that, it can be weaponized and used for pretty nefarious purposes. [The FBI] probably dodged a bullet.”
Source: washingtonpost.com




