
Top Trump ally and consistent encryption scaremonger Senator Lindsey Graham is working on a bill that could coerce tech companies to stop providing end-to-end encryption by threatening them with massive legal liability, The Eliminating Abusive and Rampant Neglect of Interactive Technologies Act of 2019 (or EARN IT Act).
The draft version of the EARN IT Act, which has not yet been formally introduced but is reportedly being circulated by Graham and Democratic Senator Richard Blumenthal, bills itself as a way to fight the distribution of child sex abuse material (CSAM) on major platforms. But it does so by threatening Section 230, a core building block of the modern internet that shields tech platforms from liability for user-generated content (for example, it’s why Gizmodo is insulated from libel lawsuits stemming from what happens in the comments section). The EARN IT Act would threaten tech companies like Facebook, Google, and WhatApp’s Section 230 immunity regarding CSAM unless they comply with a set of so-called “best practices” determined by a 15-member commission. Those companies deemed not in compliance would have the evidentiary standard used to determine whether they enable CSAM lowered from “knowingly” to “recklessly,” with the draft bill also amending Section 230 to no longer prohibit state prosecutors from pursuing criminal charges against internet companies currently protected from state laws under the statute.
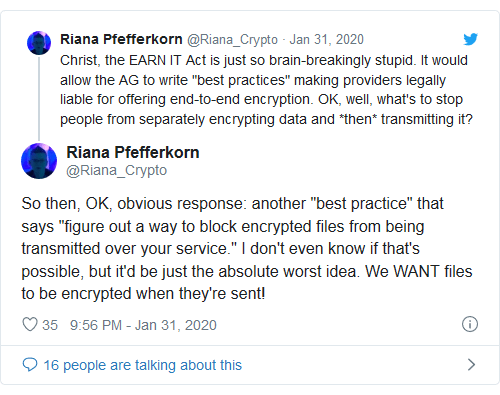
This is a disconcerting proposal for numerous reasons. As Riana Pfefferkorn of Stanford University’s Center for Internet and Society explained in a lengthy blog post, it appears to be a bait-and-switch for Congress and the Department of Justice to wage their war on end-to-end encryption by requiring those “best practices” to “condemn end-to-end encryption.” Unlike telecommunications firms like phone companies, internet platforms are exempted under federal law from having to provide the ability for law enforcement to wiretap their networks. The EARN IT Act provides a convenient workaround to bypass that.
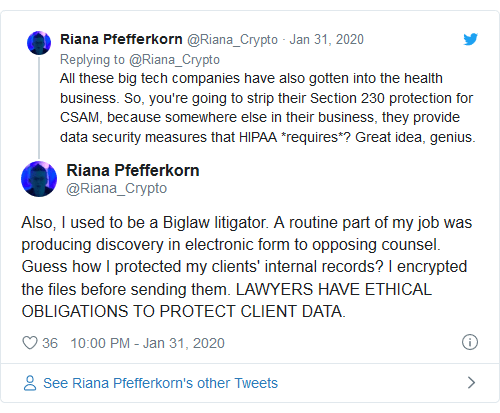
Tech companies already can be held civilly and criminally liable for CSAM on their networks under federal if they don’t comply with Chapter 110 of Title 18 of the U.S. Code, Sections 2258A and 2258B. Those sections implement requirements that platforms alert authorities and preserve evidence when they discover CSAM, providing them with legal protection if they do. All of the major platforms comply with Section 2258, Pfefferkorn wrote, and generally only underground operators involved in trafficking CSAM don’t.
The draft version of the EARN IT Act ignores that Section 2258 already provides a way for the feds to hold tech platforms accountable. Instead, it ravages the separate Section 230 immunity for CSAM unless they comply with those “best practices.” The 15-member commission that would design those “best practices” would include four law enforcement representatives, four tech industry reps, two reps of child safety organizations, and two computer scientists/software engineering experts. Moreover, the U.S. attorney general would have the power to unilaterally overrule the commission’s rulings at any time and substitute their preferred list.
In other words: Do what we say, or we’ll take away your shield from liability in civil and state criminal claims about child abuse. The bill does provide recourse in that tech companies can ignore the commission or A.G.’s requirements and implement their own “reasonable measures,” a vaguely worded provision that Pfefferkorn noted would have to be duked out in court.
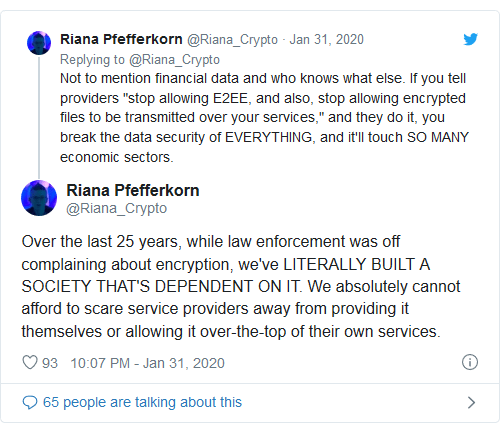
It doesn’t take a genius to see where this is going. The federal government, and especially the DOJ, have wanted tech companies to build surveillance backdoors into their end-to-end encrypted messaging services for years. They insist that they are only interested in preventing major crimes like terrorism or sex trafficking, but in reality building those backdoors would create a convenient pipeline for domestic surveillance. Under the EARN IT Act, an unaccountable 15-member commission or the attorney general (currently anti-encryption fanatic Bill Barr) could claim that end-to-end encryption goes against “best practices” and punish platforms that use it. They could also claim that the “best practices” are to build those surveillance backdoors—which would expose the content of those networks to anyone who discovered them, not just the U.S. government.
What isn’t clear is whether the act would be a big enough cudgel to force tech companies to comply, as it only revokes Section 230 protections as they apply to CSAM, Jeff Kosseff, a cybersecurity professor at the U.S. Naval Academy and author of the Section 23 book The Twenty-Six Words That Created the Internet, told Gizmodo via phone.
“What this bill is saying is for these specific types of lawsuits and criminal prosecutions you wouldn’t get Section 230 protections unless you comply with the guidelines,” Kosseff said. “I’m not sure how big of a threat this type of lawsuit or prosecution would be for the platforms to get them to—to make that tradeoff.”
“The other thing to keep in mind is that Section 230, by its terms, does cover private messaging,” Kosseff added. “It’s ‘interactive computer services’, and that would cover messaging, private email, that sort of thing. But in reality there’s only been a few cases where Section 230 has actually been applied by courts for private messaging. So there are a lot of end-to-end encryption messaging providers that frankly don’t care all that much about Section 230... I think the platforms that would care the most would be the ones that have both public-facing platforms where Section 230 matters as well as messaging services.”
Eric Goldman, a professor at Santa Clara University School of Law, called the Graham bill a “confusing mess” that strains to link perceived issues surrounding end-to-end encryption with criticism of Section 230. “There’s like six different moving parts to it. It’s kind of like a 4-D chess move to see how we get from end-to-end encryption all the way back to Section 230 for a federal crime that’s already not covered by 230,” he said, adding: “The whole structure of the [EARN IT Act] is kind of the wrong framing.”
“Let’s assume for a moment that the unavailability of Section 230 is effectively a death sentence for most companies,” added Goldman. “It’s a fast road to bankruptcy. So is that the right remedy for whatever missteps a company might make?”
There’s other issues with the draft bill as well. Both Goldman and Kosseff said it was unclear whether WhatsApp, which is owned by Facebook, would have to comply with the EARN IT Act for Facebook, the platform, to receive full Section 230 protections. The draft bill also concentrates power in the attorney general’s office in a manner that might not even be legal and leaves room for next to no input from tech companies.
“The idea that Congress can delegate virtually unilaterial authority to the [attorney general] to make rules is confusing,” Goldman said. “I’m not an expert in procedure, but I’m not sure that’s even possible. The absolute power in the AG’s hands to disregard the recommendations of the commission makes the commission a form of theater, I think. I don’t understand why go through the exercise if the AG can just do whatever he or she wants.”
“The composition of the committee is so structurally biased against most of the internet ecosystem that it’s not possible to really believe it would ever speak for the internet in a useful way,” Goldman added. “The internet is far more than Google or Facebook and so the fact that there’d be two voices for the entire rest of the internet, it’s really kind of baffling how anyone thinks that would be helpful.”
Pfefferkorn argues that because the feds can already punish tech companies that don’t do enough to fight CSAM under Sections 2258A/2258B, there’s no reason to target Section 230 other than that it’s taken center stage in politically motivated battles over online speech and censorship.
“This bill is a cynical ploy to exploit current anti-Section 230 sentiment in order to achieve an unrelated anti-encryption goal (one which, by the way, would be disastrous for cybersecurity, privacy, the economy, national security),” Pfefferkorn wrote. “Congress should not kill the freedom to encrypt by taking advantage of Section 230’s current unpopularity to get away with a bait-and-switch.”
Blumenthal hasn’t currently signed on to the draft version of the bill, according to Bloomberg. The news agency noted that while the current opposition to encryption is bipartisan, it’s unclear whether Congress would risk passing the EARN IT Act during an election year, when the assuredly heavy opposition to it could pose an immediate political price.
Source: https://gizmodo.com/lindsey-graham-is-quietly-preparing-a-mess-of-a-bill-tr-1841394208




