Although online voting in elections has been a contentious topic for decades already, it is during the current pandemic that it has seen significant more attention. Along with mail-based voting, it can be a crucial tool in keeping the world’s democratic nations running smoothly. This is where the OmniBallot software, produced by Democracy Live, comes into play, and its unfortunate unsuitability for this goal.
Despite already being used by multiple US jurisdictions for online voting, a study by MIT’s [Michael Specter] and University of Michigan researchers points out the flaws in this web-based platform. Their recommendations are to either avoid using OmniBallot completely, or to only use it for printing out a blank ballot that one then marks by hands and sends in by mail.
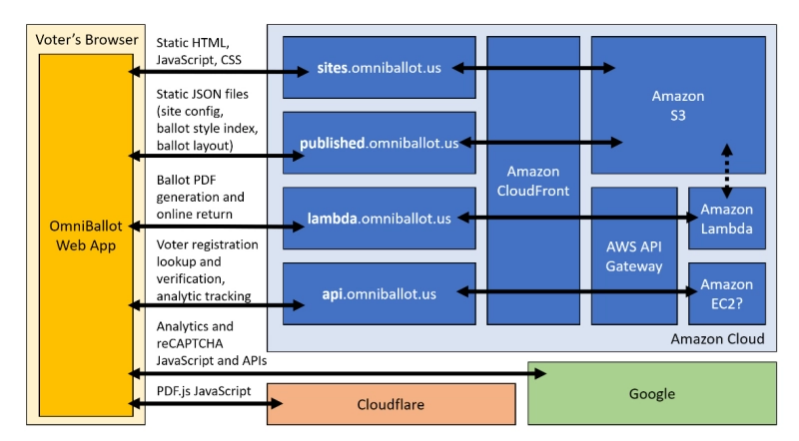
One of the issues with the software is that it by default creates the marked ballot PDF on the Democracy Live servers, instead of just on the user’s device. Another is that as a web-based platform it is hosted on Amazon Web Services (AWS), with JavaScript sources pulled from both CloudFlare and Google servers. Considering that the concern with electronic voting machines was that of unauthorized access at a polling station, it shouldn’t require a lengthy explanation to see this lack of end-to-end security with OmniBallot offers many potential attack surfaces.
When Ars Technica contacted Democracy Live for commentary on these findings, Democracy Live CEO [Bryan Finney] responded that “The report did not find any technical vulnerabilities in OmniBallot”. Since the researchers did not examine the OmniBallot code itself that is technically true, but misses the larger point of the lack of guarantee of every single voter’s device being secured, as well as every AWS, CloudFlare and Google instance involved in the voting process.
As a result, the recommended use of OmniBallot is to use it for the aforementioned printing out of blank ballots, to save half of the trip time of the usual mail-in voting.
Source: hackaday.com




